Sexists Are on Internet With Sexting Crap Again
Sexting Is Both A Pleasant And An Empowering Practice

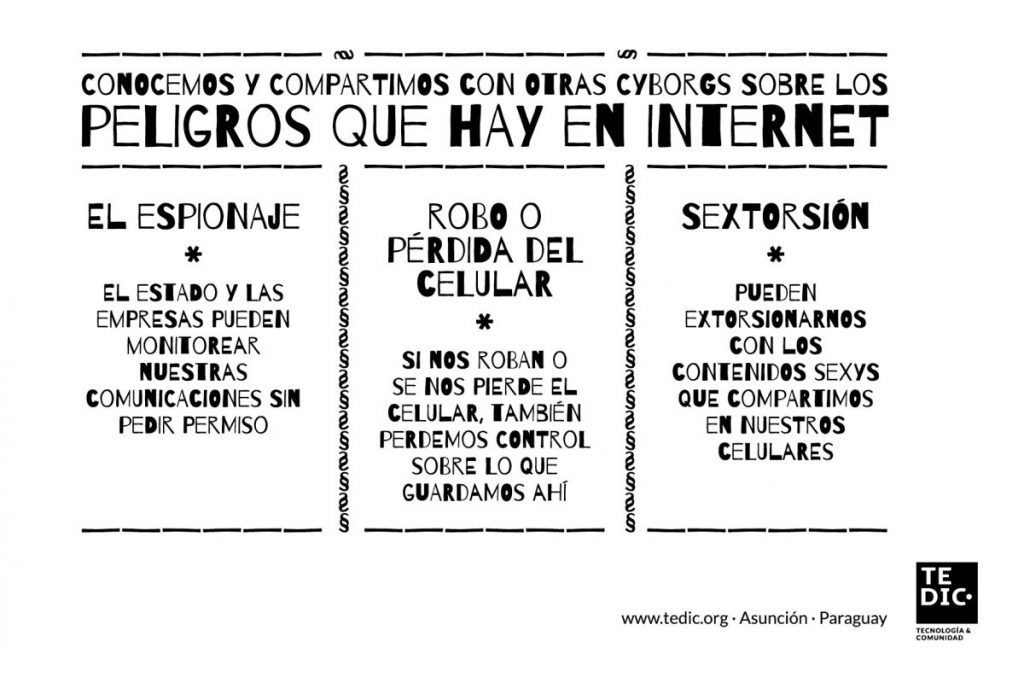
What is sexting?
When talking near sexting, nosotros probably think near information technology as taking a naked "selfie", but it is much more than that. It tin also be any kind of provocative message sent from someone's telephone or computer, such equally a photo, an audio recording or a video. This type of activity is unremarkably meant to exist a private thing, but sometimes accidents happen and something that was thought for the eyes of a sure person (or certain people), ends up being shared with third parties who were not function of the original chat.
Sexting is function of our sexual health, which is a fundamental right, more precisely a sexual and reproductive right, which affects the individual, interpersonal and social well-being of each person. Therefore, the challenge is to demand that our authorities respect and safeguard this right.
Sexting is a form of sexual liberty, which contributes to our self-decision in the field of sexuality, with no other limitation than the respect for other people's freedom. This sexual freedom is expanded past using one'south own body at will, post-obit any called sexual orientation at whatsoever given time or making and accepting proposals that arrange us, as well as rejecting unwanted ones.
According to WHO, regarding sexual wellness, a positive and respectful approach towards sexuality and sexual relations is necessary, as well as having the possibility of obtaining pleasure and enjoying safety sexual experiences, costless of coercion, discrimination and violence. For sexual health to be achieved and maintained, the sexual rights of all people must be respected, protected and fulfilled.
Sexting also ways exercising the right to liberty of expression and privacy, in addition to being considered a pleasant human activity of resistance against racism, sexism, machismo, conservatism and heteronormativity.
Is sexting okay? Isn't it a bad thing?
The key to sharing intimate images is consent. However, as the site acoso.online points out, "even if you consented to capture the images, this is not equivalent to consent its storage nor the distribution of such material«. So sexting is just legal when it involves consent. That means that nude videos or photos taken, stored and/or distributed without the cognition of the person are illegal. Constantly harassing someone or otherwise pressuring them into sending a nude photo or video is also illegal.
Sexting generally occurs between people who freely agree to it, however, there are situations where one person manipulates the other into sending them a sexy snap. If you experience pressured to sext, you may exist suffering harassment or extortion. You should never be pressured into engaging in any type of sexual action that yous don't feel comfortable with.
Sexting does not involve risks past itself, but in practice it tin become problematic, leading to many complicated situations: violation of our rights to privacy or liberty of expression, violation of our sexual rights through extortion (misnamed 'revenge porn') or distribution of intimate images without consent, equally well as the publication of personal data without dominance. At that place may also be stigmatization of the woman'south body: the tendency is to vilify, denigrate and blame the woman as the sole responsible for events that could torment her for the residuum of her life. All of these are forms of violence that limit and put at hazard sexual enjoyment, blaming the victim for the potential negative consequences of sexting.
In other words, the problem is not sexting, only the sexist behavior of those who spread images, messages and videos without consent, ignoring the responsibility assumed in the prior understanding by the people who perform sexting, and the rights of the other person.
3 aspects of sexting: how you lot sext, where you lot sext and with whom yous sext
The central to sharing intimate images is prior consent and agreement. Therefore, people who sext should at the same fourth dimension accept care of themselves and assume the responsibility of taking intendance of the other person. Make certain that the three stages of sexting are clear in the understanding: the registration of the epitome (or text, or video), its storage and its distribution.
Tip ane: Nosotros accept accented control over every message nosotros send, be it a sexy text or an intimate image or video. They may include our face, our total body or item parts of the body, and these may be displayed in a covered, explicit or artistic way. Imagination is in our power.
Tip two: Allow's choose our tools well. It is not recommended to sext through unknown or unsafe mobile apps which practise not include a deletion pick, and/or don't feature anonymization or encryption. For a gratuitous and safe sexting, carefully select a tool that offers the best standards for the protection of your rights.
Tip 3: Trust is cardinal, but its elapsing may vary for each given relationship, and information technology is important to be aware of the risks that this tin can entail. Depending on the person, sexting can exist done with people we know well or with people we know not-and then-well (contacts from Facebook, Twitter, Tinder or Grindr). Therefore, it is of import to be aware of the correct handling of identities and anonymity in sexting in gild to reduce the take a chance of violence on the Internet.
What to exercise if images are nonconsensually disseminated?

First of all, nosotros must bear in heed that sexting has shared responsibility equally one of its main characteristics. Therefore, on meridian of sexting securely, we should not violate later on the prior agreements regarding its nonconsensual storage or dissemination.
This entails legal consequences that may include complaints of harassment (private criminal action), violation of privacy, personal data, transfer of prototype (intellectual property), gender violence, among others. If it happens on the Internet, try to report the example through the contact lines of the website or social network. If you are yet concerned, nosotros recommend that you speak to a trusted person and/or the police.
Secondly, the cycle of sexual violence should non be fueled. When facing this kind of outcome, the victim must be supported, the person who disseminates the images must be reported and, above all, the images must not be reproduced through other channels or networks. The culprit is not the victim, simply the one who broke the trust agreement and produced that act of sexual violence.
Diamonds are forever, and so are your sexy pics. What to do to reduce the risks.
There are technological tools that can help you lot protect yourself, then information technology's of import to sympathize the legal shields that each app has to defend your digital rights.
Tip 1: Anonymize

Anonymity is a right that helps guarantee other fundamental rights, such as protecting our privacy, expressing ourselves, coming together with others, seeking information, seeking aid and, of course, sexting.
1.ane Edit: Use stickers to embrace or cut out signs that can help identify you, such as tattoos, a birthmark, or even your face. This will later permit yous to deny that it is you lot in the picture, in the consequence that someone violates your correct to privacy.
1.ii Delete the metadata (information about other data): Metadata is all the information that complements and contextualizes a computer file and could eventually aid identify you lot. In the case of an image, the metadata can be geolocation, jail cell phone model used, date and time, etc. To access this information, check the prototype properties or insert your pictures on the website http://metapicz.com.
To delete the metadata of cell phone images, you lot tin use ObscuraCam (developed past The Guardian Project), which allows y'all to remove metadata and likewise to mistiness parts of the picture. Y'all may also utilize Metanull or Send Reduced to remove metadata. Exist sure to follow the anonymization tips we mentioned earlier.
Something important to keep in mind when pictures are downloaded from social networks (such as Facebook, Twitter or Instagram), is that these networks commonly delete the original metadata. However, this metadata may be stored on the servers of these companies.
i.three Clear traces when browsing: To avert leaving traces, use browsers in incognito (or individual) style. This prevents both browsing data (history, cookies, searches, etc.) and passwords from beingness stored. So, if you forgot to log out of any web page or social network, don't worry, nobody will be able to admission it.
Keep in heed that browsing too shares information with Cyberspace providers through the connection's IP address. For example, you can see your current geolocation using the web tool https://whatismyipaddress.com.
1.four Anonymize your IP: One stride further could exist anonymizing your IP address through the Tor browser or a VPN (Virtual Private Network 1 ). In that location is besides the possibility of using the 'amnesic' and incognito operating system called Tails.
One time you install any of these tools on your prison cell phone or reckoner, bank check that your Internet access no longer corresponds to your actual state. As mentioned above, you can use https://whatismyipaddress.com.
Tip 2: Encrypt Your Communications And Devices
- Always browse sites that apply the secure Internet protocol 'HTTPS'. This often looks like a tiny padlock on the left of the accost bar.
- If you sell your phone, reset it to manufactory defaults to prevent people from accessing your files.
- Keeping your devices updated is very important, as information technology may fix vulnerabilities and prevent unwanted admission.
- Encrypt your devices to prevent access to your sensitive information in the event of theft or loss.
- When eliminating images or videos, be certain to too eliminate backups. Some cell phones and apps create automatic backups, then it is advisable to check that they likewise disappear.
- Employ apps that include end-to-end encryption. This means that the advice between two or more cell phones is encrypted in a way that no one else can access the information. It is as if they speak a language that no one else knows, not even the company that provides the service. Some apps that employ finish-to-terminate encryption are Signal, WhatsApp, Facebook messenger and Telegram (optional).
- Use Jitsi or WhatsApp for video sexting. Jitsi is a spider web platform that offers HTTPS encryption and allows users to create temporary rooms for voice and video chat, without the need to install anything on the calculator or device.
- Avoid sending text messages or making phone calls, equally all the information volition exist stored by your telephone service provider. Chat apps similar Signal or Whatsapp also include point-to-point encryption in calls. At that place have been reports nearly cases where employees of telephone companies published conversations of couples in order to brand fun of them.
- Use apps that allow you lot to have the highest level of control, such every bit the possibility of remotely deleting images, using the message fading office or receiving screen capture alerts. Some apps that include this are Signal, Telegram, Instagram and Whatsapp (in their more than recent versions), with deletion permission up to 7 minutes subsequently sending.
If y'all desire to know more, check the presentation we made for a workshop on sexting:
Notas:
- Read our article on VPN (in Spanish): https://world wide web.tedic.org/la-vpn-como-forma-de-libertad/
Source: https://cyborgfeminista.tedic.org/sexting-self-care-on-the-internet-sendnudes/
0 Response to "Sexists Are on Internet With Sexting Crap Again"
Post a Comment